We are currently undergoing maintenance on our email server. Kindly direct your emails to us at alaintester003@gmail.com. We apologize for any inconvenience caused.
Cyber Security
Cybersecurity is essential to protect sensitive information and systems from unauthorized access, attacks, and damage. It helps safeguard personal data, financial assets, and critical infrastructure, ensuring privacy, maintaining trust, and preventing costly breaches and disruptions.


Security Posture Assessment
A Security Posture Assessment (SPA) aims to evaluate the existing security baseline of the network and systems by identifying known vulnerabilities and weaknesses. The goal is to implement gradual enhancements to strengthen the overall security of the network and systems.
- Identify Vulnerabilities: Detect and document known weaknesses and vulnerabilities in the network and systems to understand the current security landscape.
- Evaluate Security Measures: Assess the effectiveness of existing security controls and measures to determine if they are adequately protecting against potential threats.
- Prioritize Risks: Analyze and prioritize identified vulnerabilities and threats based on their potential impact and likelihood, enabling focused remediation efforts.
- Establish Baseline Security: Create a baseline of the current security posture to track improvements and measure the effectiveness of implemented security enhancements.
- Recommend Improvements: Provide actionable recommendations for enhancing security, including incremental changes to strengthen defenses and mitigate identified risks.
- Monitor and Review: Implement continuous monitoring and periodic reviews to ensure that security improvements remain effective and adapt to evolving threats and changes in the network environment.
Our Tools
Tools are essential for effective Security Posture Assessment (SPA) because they automate and enhance the process of identifying vulnerabilities, evaluating security measures, and analyzing potential risks.

Nikto
A web server scanner that identifies vulnerabilities and security issues.

NMAP
A network scanning tool used for discovering hosts and services and detecting open ports.

Tenable Nessus
A vulnerability scanner that assesses network and system vulnerabilities.

Burp Suite
A web vulnerability scanner and testing tool for identifying security flaws in web applications.
WireShark
A network protocol analyzer that captures and examines network traffic for suspicious activity.

SQLmap
A tool for detecting and exploiting SQL injection vulnerabilities in databases.

Kali Linux
A penetration testing and security auditing platform that includes a wide range of tools for SPA.

Metasploit
A framework for developing and executing exploit code against vulnerable systems, aiding in penetration testing and vulnerability assessment.

OpenVAS
A comprehensive vulnerability scanning and management tool that helps identify and address security weaknesses across systems and networks
Streamlined, Efficient, Reliable
what our clients have to say
"We have been thoroughly impressed by the company's security testing services, which have surpassed our expectations in uncovering vulnerabilities and fortifying the strength of our software. "
Malaysian Administrative Modernisation and Management Planning Unit (MAMPU)Client 
"AL AiN expertise and meticulous attention to detail surpassed our expectations, making them our top recommendation for anyone seeking top-notch security solutions."
Malaysian Industry-Government Group for High Technology (MiGHT)Client 
"AL AiN's exceptional expertise and unwavering attention to detail exceeded our highest expectations, positioning them as our premier recommendation for anyone in search of unparalleled security solutions."
Lembaga Hasil Dalam Negeri Malaysia (HASiL)Client 
"The unmatched expertise and meticulous attention to detail from AL AiN have set a new standard for excellence, making them our leading recommendation for top-tier security solutions."
Telekom Malaysia BerhadClient 
Intelligence-led Pentest
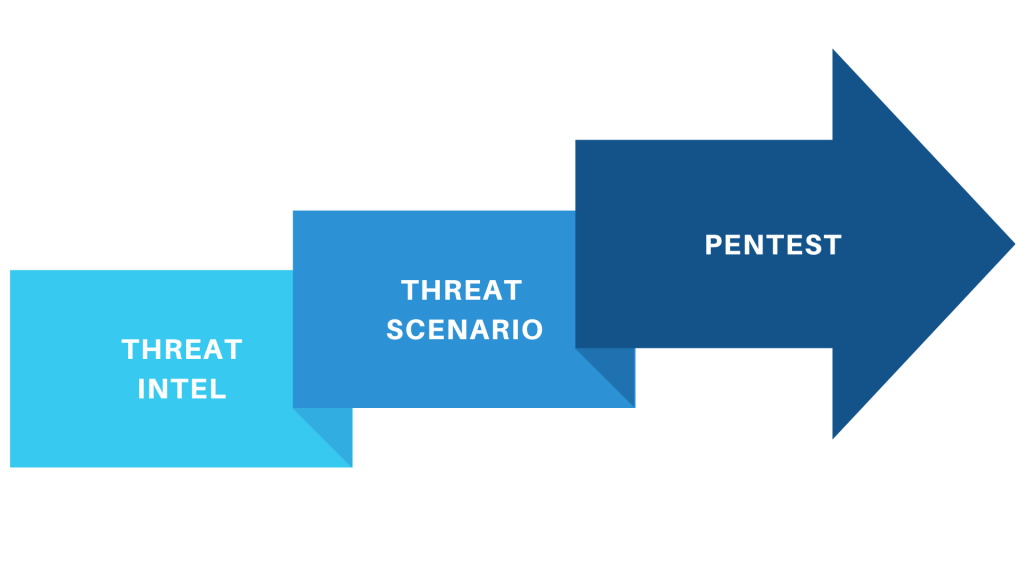
Organizations needing targeted, intelligence-driven penetration testing must first conduct a Threat Intelligence phase. During this phase, critical systems and functions will be examined for potential threats. Recent threat intelligence from various sources, along with historical attack data, will be analyzed to identify the most likely threats. Based on this analysis, a list of potential threat scenarios will be developed.
The penetration testing team will then design assessments tailored to these threat scenarios. Depending on the identified threats, the assessments may include external penetration testing, web application assessments, data exfiltration exercises, or social engineering tactics.
augmented validation of security assessments
Augmented validation of security assessments involves using advanced technologies, continuous monitoring, and expert analysis to enhance the accuracy and effectiveness of security evaluations. It combines automated tools with manual techniques and independent reviews to ensure thorough and up-to-date security coverage.
Benefits of Augmented Validation Of Security Assessments :
- Enhanced Accuracy and Reliability: Augmented validation improves the accuracy of security assessments by combining multiple validation techniques and tools. This reduces the likelihood of false positives and negatives, ensuring a more reliable assessment of security posture.
- Adaptation to Evolving Threats: Cyber threats are constantly evolving, and traditional assessment methods may not keep pace. Augmented validation leverages advanced technologies, such as AI and machine learning, to stay ahead of emerging threats and adapt to new attack vectors.
- Comprehensive Coverage: Augmented validation incorporates various approaches, including automated scanning, real-time monitoring, and expert analysis, to provide a more thorough evaluation of security. This ensures that all potential vulnerabilities and attack vectors are identified and addressed.
- Improved Response Time: By integrating continuous monitoring and real-time analysis, augmented validation enables faster detection and response to security incidents. This proactive approach helps mitigate potential damage and reduces the time to address vulnerabilities.
- Reduction of Human Error: Automated tools and advanced technologies in augmented validation minimize the impact of human error in security assessments. This ensures that assessments are conducted consistently and thoroughly, reducing the risk of overlooked vulnerabilities.
- Objective Evaluation: Engaging independent third-party assessors for augmented validation provides an objective evaluation of security measures. External experts can offer unbiased insights and recommendations, enhancing the credibility and effectiveness of the security assessment process.


